04. Defense in Depth Introduction
Defense in Depth Introduction Heading
Defense in Depth Introduction
ND545 C02 L01 A04 Defense In Depth Introduction
Defense in Depth Introduction Notes
It is not necessarily the quantity of layers, although more can certainly be better, it's about the quality of those layers. And the better those layers work together, the more effective they are. For example, in subsequent lessons you will see how firewalls act as the perimeter defense and Intrusion Detection Systems are the perfect fit for the next layer.
Key Concept
Defense in Depth is using complementary layers of defenses to protect your organization.
Defense in Depth Introduction New Terms or Vocabulary
Additional Resources
Defense in Depth Introduction Image
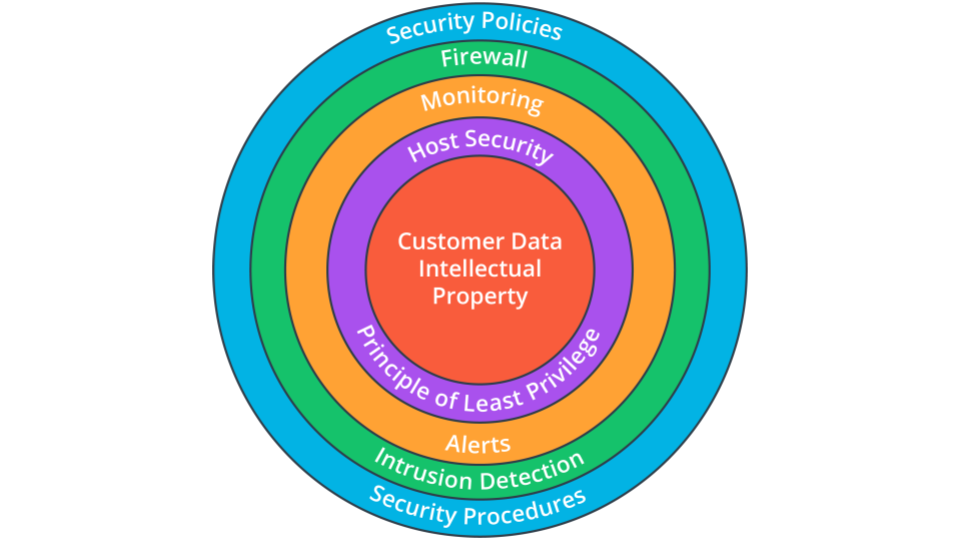
Defense in Depth uses overlapping layers of security to help protect what's most important.
We just introduced the 3-Component model of security with Prevention, Detection and Response making up the three parts. All topics in this course will match up with at least one, possibly more, of these components. All 3 of the components are required as they work together to effectively protect your organization.
ND545 C02 L01 A05 Defense In Depth Introduction Walkthrough
Defense in Depth Introduction Further Research
This walkthrough illustrates in a slightly more focused context, the way the various layers of security work together to form a solid defense. Cybersecurity operates much like a fractal. It has layers when zoomed out at a macro level, think a full organization view, however when you zoom in you still see layers of security.
Addtional Links
For a deeper dive into securing web servers visit the link below.